Phishing has been around as long as email, and it continues to present a substantial risk to business and is often cited as a top security concern. The concern is driven by increasingly sophisticated attacks; the move from email to alternative attack vectors, such as social media and messaging; and the simple fact that phishing targets the weakest link in the security chain: people.
The 2019 Verizon Data Breach Incident Report (DIBR) established a correlation between phishing and stolen user credentials in the vast majority of reported data breaches. Why should attackers bother looking for ways to bypass your business’s security controls when they can simply walk in the front door with user credentials harvested from a phishing attack?
Fortunately, there are a few things you can do can you protect your organization.
It's not just about email anymore
The Anti-Phishing Work Group defines phishing as social engineering schemes that use spoofed emails purporting to be from legitimate businesses and agencies to lead consumers to counterfeit websites that trick recipients into divulging data such as usernames and passwords.
Unfortunately that definition is from an age when email was the only phishing attack vector that businesses needed to protect. Phishing attacks that use social media and messaging to launch and amplify an attack are on the increase. And in case you are thinking that’s only relevant for consumers, attackers are using Skype, Slack, Microsoft Teams, LinkedIn, and many other business messaging and social apps to launch targeted spearphishing or business email compromise (BEC) attacks.
The phishing arms race
Protecting against phishing attacks is an arms race that is constantly evolving. No sooner is one type of phishing thwarted than it’s replaced with others using different approaches. Attackers are sophisticated and continue to look for ways to thwart security defenses.
For example, attackers found a way around Office 365 email protection, evading its link replacement capability by embedding zero-width characters into the phishing URL. That meant the system delivered the email with the phishing link intact instead of replacing it with a Microsoft-hosted link.
Another approach is to send emails from “reputable” Office 365 accounts that have been compromised. Because the emails originate from a reputable source, email filters don't block them.
In another example, a compromised, company-owned device sent out phishing emails. Since internal emails don’t use the Simple Mail Transfer Protocol (SMTP) and are simply a mail server database update, the company's email filter did not block them.
Another way attackers gain credibility is by making their phishing page use SSL encryption. Sadly, we have educated users to assume that, if they see an SSL padlock symbol in their browser, the page is safe.
Lastly, attackers are using URL redirection to obfuscate phishing links. According to a recent report from the Anti-Phishing Working Group, “MarkMonitor is detecting an increase in the use of redirectors, placed both prior to the phishing site landing page and then following the submission of the credentials as well.”
The industrialization of phishing
In this everything-as-a-service world, it’s easy for attackers with zero skills to launch sophisticated phishing attacks by using widely available, low-cost phishing kits. These all-in-one software packages copy the target site, configure a cloned site, capture the information, and deliver it to the attacker.
Thousands of these kits are available at prices ranging from free to $300, and the kits are continuously adding new capabilities. Many come pre-loaded with the target site, can automatically detect the victim's device type and location, and then serve up a responsive phishing page based on those parameters.
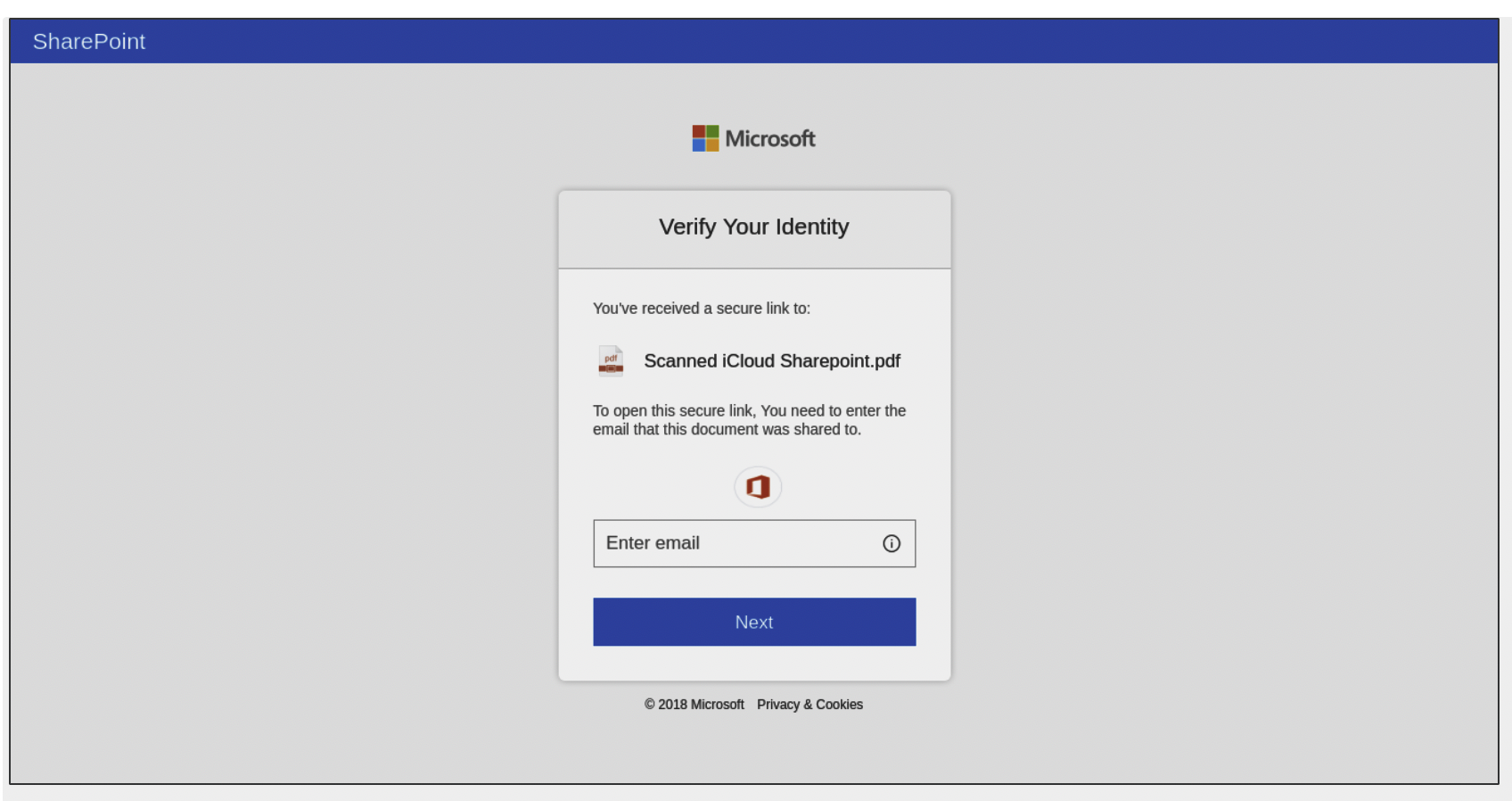
Until recently, these kits targeted consumers. One example of this is a phishing kit-based attack that tricked consumers into believing they could win free airline tickets. Now, however, those same techniques are being used to target enterprises with, for example, this near-perfect clone of a Microsoft SharePoint login page.
The attack flow is simple: rent a compromised web server or use a hosting provider, upload and configure your phishing kit, and send your phishing emails. Victims then enter credentials, which the system emails directly to the attacker, granting them the keys to your front door.
How existing phishing defenses are being exploited
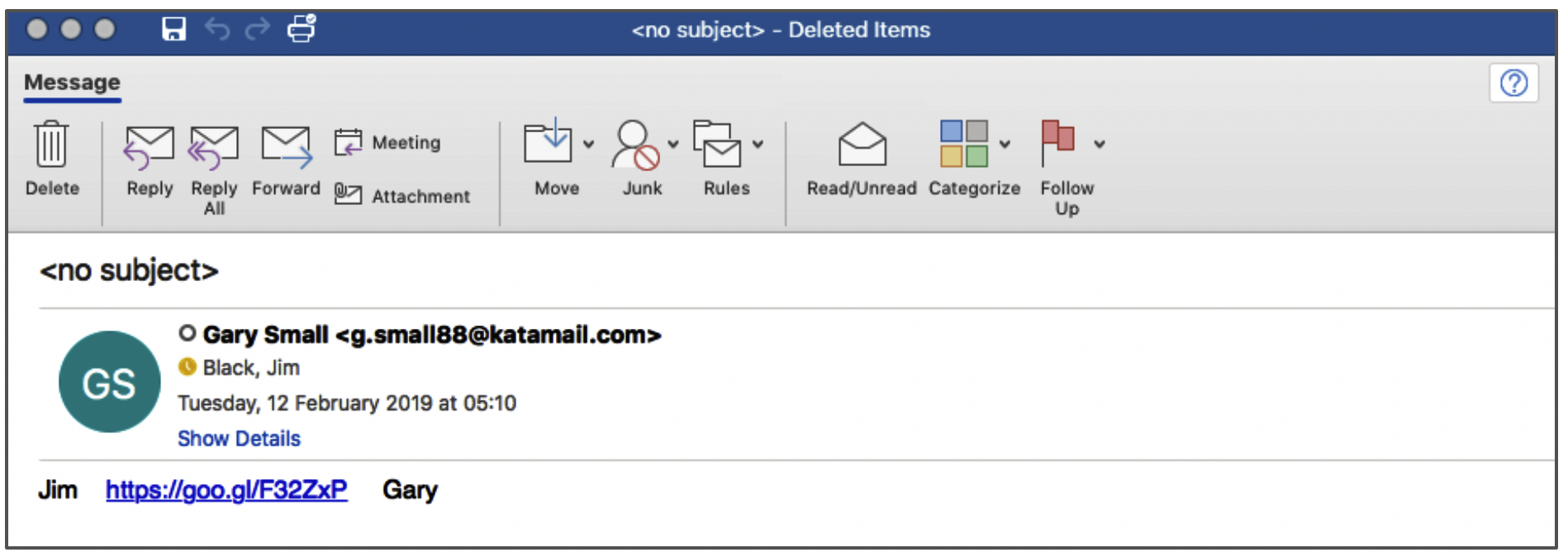
Every business has some form of email filtering or email gateway in place, either as a dedicated service from an email security company or as an additional service dedicated to Office 365 or Google. These products are generally pretty good at blocking spam, phishing, and malicious emails, but are far from perfect, as the below example shows.
This is a pretty obvious phishing email, so why wasn't it identified and blocked? The main reason is that email filters are good at blocking emails that exactly match the signature of emails the system has seen before. This is irrespective of the types of techniques that are used to identify and block emails—all enterprise email filters use numerous techniques and layers of protections.
Timing is critical
My threat research team recently undertook a project to better understand how attackers exploit existing defenses. One of our most significant findings: There is a gap between the time a new phishing website is launched and when the offending URL is identified by security companies and added to a blacklist. The result: Although the phishing domain may have been created for some time, the domain won't be added to a block list until the system observes traffic being directed toward the domain. So by the time the domain has been added to the blacklist, attackers are already using new domains. Attackers exploit this time-to-identify technique by registering and creating hundreds, or thousands, of domains, each for a short period of time. That's why timing is critical to stop these kinds of attacks.
The availability of off-the-shelf phishing kits has allowed attackers to create sophisticated, short-lived campaigns targeted at enterprise users. Current phishing protections are often ineffective, so enterprises need new ways to increase their defenses. Here are two:
- Consider using a service that inspects all of an enterprise's recursive DNS traffic for requests to phishing pages, regardless of how the phishing link was delivered. Deploying that service in addition to an existing email gateway delivers a defense-in-depth approach against phishing.
- Use a service that can examine the requested web page in real time, at the point of request, to identify pages that have been built using a phishing kit.
Such techniques could potentially protect your organization from the increasingly sophisticated, advanced phishing attacks. Phishing is not just about email attacks on consumers anymore, and your organization needs to be prepared for that.
Keep learning
Learn from your SecOps peers with TechBeacon's State of SecOps 2021 Guide. Plus: Download the CyberRes 2021 State of Security Operations.
Get a handle on SecOps tooling with TechBeacon's Guide, which includes the GigaOm Radar for SIEM.
The future is security as code. Find out how DevSecOps gets you there with TechBeacon's Guide. Plus: See the SANS DevSecOps survey report for key insights for practitioners.
Get up to speed on cyber resilience with TechBeacon's Guide. Plus: Take the Cyber Resilience Assessment.
Put it all into action with TechBeacon's Guide to a Modern Security Operations Center.