Want to know how to make money quickly without any investment? While it sounds like a cheap come-on, it's really not: Security researchers can use continuous integration (CI) servers as a means for collecting bug bounties, and more.
The goal of this exercise, of course, is to show you how resources can be used outside of their intended use case in a malicious way. And the ultimate result, I hope, is to use threat modeling to identify these edge cases and understand how the vulnerabilities can be remediated prior to publicly releasing such software.
And now back to the servers. CI is the action of merging small pieces of work created by developers into a larger codebase, creating the final product that clients and end users see. The idea behind CI is to promote smaller and faster updates to codebases. This allows large organizations to create smaller teams and tackle problems in an effective manner.
CI servers are used as pipelines to test and ensure that code committed to a central repository meets predefined standards. These checks follow a programmatic process. Examples of such checks can include PEP8 checks, unit tests, and testing benchmarks.
For my upcoming talk at DevSecCon Seattle, I'll concentrate on Travis CI as both a product and a target. Why Travis CI? The open-source version is completely free, it allows an unlimited number of commits, allows unlimited of repositories, and has a maximum build time of 50 minutes. (There's also a commercial, or closed, version of Travis CI.)
So how does a free service make you money? You can use Travis CI to exploit bug bounties for income, and you can generate income with the Travis CI containers themselves.
When bugs are bountiful
For bug bounties, you want to submit high-severity findings, which encourages the target organization to pay the bounty due to the impact. For the purpose of my talk, I will focus on information disclosure within the public Travis CI instances.
There are two major avenues for information disclosure within open-source projects. First is disclosure of information within configuration files and source code (detectable with tools such as TruffleHog and GitAllSecrets).
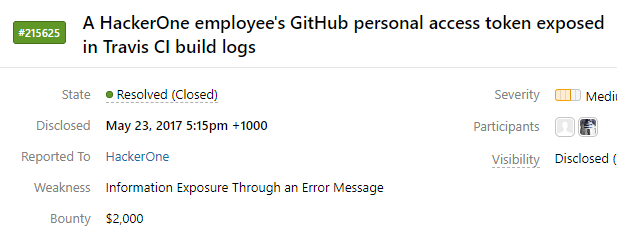
Second, you can look into the information disclosed during the execution of the Travis CI pipeline. An example of valid information disclosure within the Travis CI logs appears below:

By using tools such as CDL's secretz, you can easily extract all logs for any public Travis CI instance. Then you can simply run "grep -nir Token" to search recursively through all log files and attempt to determine sensitive information.
Using this method, I have found valid AWS API keys and secrets, providing access to the organization, which could lead to significant damage if used maliciously.
[ Special Coverage: DevSecCon Seattle 2019 ]
How to hack containers for money
Alternatively, you can attack the containers themselves. While performing a thorough analysis of the Travis CI containers (while researching), you can see that there are several flaws within the Travis CI container security posture. The following flaws were identified at the time of researching:
- Containers can be used as proxy servers to siphon malicious traffic.
- It may be possible to escape the container using a Docker escape of sorts. (I was not able to perform this.)
- Logs were removable by any collaborator permanently.
- Information leakage was prevalent within the build scripts and logs.
- I observed the ability to perform distributed denial-of-service attacks from within the containers.
My DevSecCon Seattle talk will dive into how each of these flaws works and how they can be used maliciously (hypothetically). In the context of making money out of thin air, any service that can benefit from free CPU cycles will yield good income. Some examples of such services are:
- Distributed bitcoin mining
- Distributed password-cracking services
- Distributed denial-of-service attack services
Finally, you can attempt to find possible ways to remediate each flaw identified using core threat modeling techniques.
Secure software is the goal
Hopefully people can now understand how to think about securing their software more effectively.
Travis CI is a great piece of software and one of the few that have taken a stance to help make the open-source world a better place. Thanks for being awesome, Travis CI.
Come to my presentation at DevSecCon Seattle 2019, where I'll dive deeper into how to use CI tools for nefarious purposes, and in so doing help secure software better. The conference runs September 16-17, 2019.
Keep learning
Take a deep dive into the state of quality with TechBeacon's Guide. Plus: Download the free World Quality Report 2022-23.
Put performance engineering into practice with these top 10 performance engineering techniques that work.
Find to tools you need with TechBeacon's Buyer's Guide for Selecting Software Test Automation Tools.
Discover best practices for reducing software defects with TechBeacon's Guide.
- Take your testing career to the next level. TechBeacon's Careers Topic Center provides expert advice to prepare you for your next move.