Sensitive data is often not protected as well as it should be. This often results in a large-scale data breach, even though the sensitive data may be encrypted. This happens because the most common approaches to encryption provide absolutely no protection against the serious threats posed by advanced persistent threats (APTs) and malware.
To understand the limitations of the most commonly used types of encryption, think in terms of an "encryption stack" that parallels the familiar protocol stack that forms the basis of today's Internet.
How the encryption stack stacks-up
The TCP/IP protocol stack is used in most of today's computer networks. One notable feature of TCP/IP is how it abstracts the functionality of a network into four layers that form the "stack."
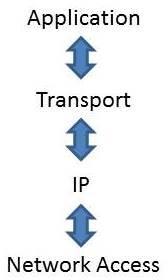
As defined in RFC 1122 and RFC 1123, TCP/IP consists of four layers: Application, transport, IP, and network access (sometimes called the Link layer), as shown in Figure 1. As the arrows below suggest, information passes only between adjacent layers of the TCP/IP stack. So a process running at the transport layer can pass information to a process running one layer away at the IP layer, but not to one running two layers away at the network access layer.
Figure 1. A conceptual model of the TCP/IP protocol stack.
Similarly, it's useful to think of encryption as taking place either relative to or at different levels in the TCP/IP stack, thus creating a notional encryption stack that closely parallels TCP/IP.
The Transport Layer Security (TLS) encryption used by secure websites, for example, operates between the Application layer and the Transport layer. Internet Protocol Security (IPsec) encryption, used to create virtual private networks (VPNs), operates at the IP layer. Link encryptors encrypt at the network access layer. Full-disk encryption (FDE) operates below the network access layer, as does transparent database encryption (TDE).
Why you need to encrypt on all layers
There are good reasons to encrypt at different places in the TCP/IP stack, but understand that when you encrypt at a particular place in the stack, the encryption protects only against threats that target layers at or below where the encryption takes place. Once data passes up the stack to a higher layer, any encryption at lower layers no longer protects it.
If you protect data with FDE, for example, the encryption will protect the data while it is stored on encrypted disks. But when the data leaves those disks and gets handed off to the network access layer, that encryption no longer protects it.
So, if a cybercriminal manages to steal a hard disk that is encrypted with FDE, they will be unable to access its contents. But if a cybercriminal intercepts information being transmitted across a network, FDE provides absolutely no data protection.
Similarly, malware that reads data from a hard drive that is protected with FDE will be totally unaffected by FDE; once the encrypted data is read from the hard disk, FDE no longer protects it.
Similarly, TDE also protects data only while it is stored in a database. When the data is read from the database, the protection provided by the encryption is lost, so attacks that operate at most levels of the encryption stack are totally unaffected by database encryption.
If you are using IPsec encryption to encrypt data at the Internet layer, IPsec encryption will protect against attacks that target the Internet layer. But once data passes up to the application layer, the IPsec encryption no longer protects it.
And if you are using TLS to encrypt data between the transport and application layers, TLS encryption will protect against attacks that target the Transport layer, the IP layer, and the Network Access layer, but processes running at the Application layer. Once data that is encrypted using TLS gets passed up the stack to the Application layer, TLS encryption no longer protects it.
Pay the most attention to the application layer
But the biggest and most severe data breaches all have one thing in common: They all operated at the application layer. Because of this, encrypting at the application layer is the only form of encryption that will address these important threats.
TLS encryption does not protect against threats that operate at the application layer. Nor does IPsec. Nor does FDE. Nor does TDE. These are the most common forms of encryption currently in use, which means that most encryption is ineffective at protecting against the most serious threats businesses face.
Because the way in which encryption is currently used by businesses does not address the most serious threats, it's likely that these technologies will also continue to provide an inadequate level of protection against the attacks that cybercriminals will attempt in the future.
But data-centric security—encrypting at the application layer—will protect against APTs and malware. These threats operate at the Application layer, so only encryption at that layer will protect against them.
It is possible to encrypt sensitive data in a way that protects against threats that lead to large, high-profile data breaches, but not all forms of encryption will do this for you. TLS will not do it. IPsec will not do it. Full-disk encryption will not do it. And transparent database encryption will not do it.
Get data-centric on your security
Don't be lulled into a false sense of security if you are using these forms of encryption. Each is very useful, but none of them will protect against the most serious threats. Only data-centric security does that, so use it to protect your data. That's is the best way to ensure that hackers never get their hands on it.
Keep learning
Get up to speed on unstructured data security with TechBeacon's Guide. Plus: Get the Forrester Wave for Unstructured Data Security Flatforms, Q2 2021.
Join this discussion about how to break the Ground Hog Day repetition with better data management capabilities.
Learn how to accelerate your analytics securely into the cloud in this Webinar.
Find out more about cloud security and privacy, and selecting the right encryption and key management in TechBeacon's Guide.
Learn to appreciate the art of data protection and go behind the privacy shield in this Webinar.
Dive into the new laws with TechBeacon's guide to GDPR and CCPA.